Event Id 4624
This phenomenon is caused by the way the Server service terminates idle connections. Select the Edit query manually on the bottom.
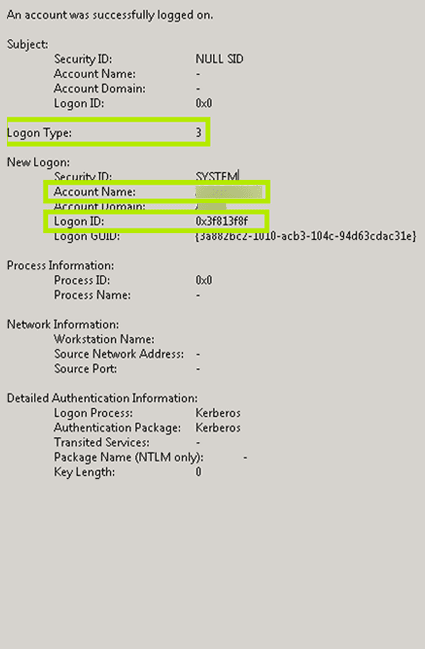
An account was successfully logged on.
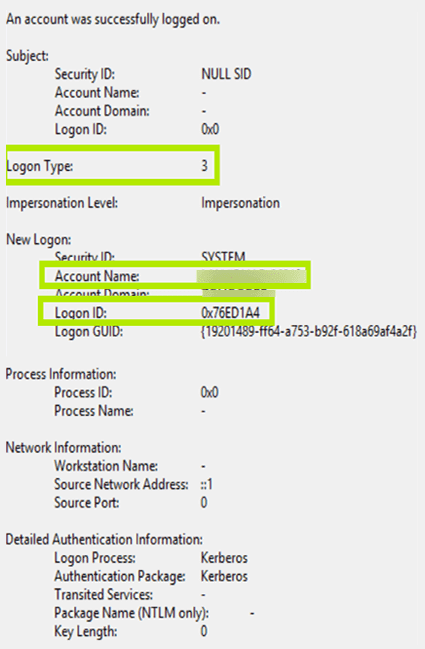
Event id 4624. 4768 4769 4624 Windows 2003 Event IDs. An account was successfully logged on. Event ID 4656 - Repeated Security Event log - PlugPlayManager.
According to the event time they happened at the exact same second. Input 4624 in the Event IDs box. An account was successfully logged on Target Account.
In the Event logs section to the right of By log select the Security Windows log. Logon ID Type HexInt64. 9302016 104837 PM Event ID.
Domain Controller- WIN1091. Look at the logon type it should be 3 network logon which should include a Network Information portion of the event that contains a workstation name where the login request originated. You will receive event logs that resemble the following.
The event will look like this the portions you are interested in are bolded. Type 3 Network when NLA is Enabled and at times even when its not followed by Type 10 RemoteInteractive aka. In Event Viewer right click on Custom Views and select Create Custom View.
This event is generated on the computer that was accessed in other words where the logon session was created. For example successful login attempts have an event ID of 4624 which are described here. Security ID Type SID.
This is a highly valuable event since it documents each and every successful attempt to logon to the local computer regardless of logon type location of the user or type of account. Your help is very much appreciated. An account was successfully logged on.
Domain Member- Event related. ItSupport Possible fake machine account. Event ID - 4624.
This example shows a successful login event generated on the accessed system when a logon session is created. I also checked and both the logon and logoff have the same Logon ID. Account for which password reset was requested.
Event ID 4624 Logon Types. Terminal Services aka. ZFaircloth Jan 26 2016 at 256 PM.
Event Id 4624 with more than 1 successful logon with logon type in 3 10 from same account name and different source network address. 28 rows Event ID. 3 FortiAuthenticator supports the following event IDs.
It is generated on the computer that was accessed. This event is generated when a logon session is created. A logon was attempted using explicit credentials and 4964 S.
Hi We have the following Advanced Audit policies configured for our domain but still we dont see the event logs with machine user logon details. Windows 2008201220162019 Event IDs. For network connections such as to a file server it will appear that users log on and off many times a day.
Although these are showing up as Event ID 4624 which generally correlates to successful logon events these are NOT successful access to the system without a correlating Event ID 4624 showing up with an Account Name domainusername and a type 10 logon code for RDP or a type 3 for SMB. This event is controlled by the security policy setting Audit logon events. This event signals the end of a logon session and can be correlated back to the logon event 4624 using the Logon ID.
Consider that you might have thousands of different. You can tie this event to logoff events 4634 and 4647 using Logon ID. Attach a task to the log Give it a name Set the action to send email enter SMTP infoemail addressetc.
For event ID 4624. Set the action to run a program and have it run a batch file that will pull the data from the event. The logon type for both is.
This event is generated when a logon session is created. The subject fields indicate the account on the local system which requested the logon. While I was looking through the 4624 4634 events in the event log I found that several times throughout the day there was a 4624 logon followed immediately by a 4634 logoff.
Event Viewer Event ID 4624 - See Who and When Logged Into My Computer1. The second Event Id is the Vista2008 Event Id For example in the Event Ids for bad password of 5294625 the code of 529 is the old Event Id while 4625 is the new Event Id. You can double check this by looking at 4625 events for.
No user action is required. Hexadecimal value that can help you correlate this event with recent events that might contain the same Logon ID for example 4624. It also can be used for correlation between a 4624 event and several other events on the same computer that can contain the same Logon GUID 4648 S.
Event 4672 Special Logon. It is generated on the computer that was accessed. An account was successfully logged on.
Event ID 4624 viewed in Windows Event Viewer documents every successful attempt at logging on to a local computer. 672 680 528 540 Support for these events is available by enabling Enable polling additional events under the Fortinet Single Sign-On FSSO section. Note that if there is no Event in the.
This is most commonly a service such as the Server service or a local process such as Winlogon. Find a logged 4624 event. To find applications that use NTLMv1 enable Logon Success Auditing on the domain controller and then look for Success auditing Event 4624 which contains information about the version of NTLM.
Event Id 4624 with logon types 10 2 Type 2 A user logged on to this computer and account name has ends with Example. Remote Desktop OR Type 7 from a Remote IP if its a reconnection from a previousexisting RDP session. Categories Active Directory Event ID Logon Audit Security Post navigation.
SID of account for which password reset was. An account was successfully logged on. Tracking User Logon Activity using Logon and Logoff Events.
Now that you have your centralized log you can setup how you want to view the information. 4624 Ta Hi Check if the Force audit policy subcategory. Select the XML tab.
A related event Event ID 4625 documents failed logon attempts. Event ID 4624. Special groups have been assigned to a new logon.
It is generated on the computer that was accessed. You will get an Event. This event is generated when a logon session is created.
For an explanation of all possible fields search for your logs event ID. The new Event Id of 4625 is generated by adding 4096 to the old Event Id -- 529 4096 4625 Workstation Logons.
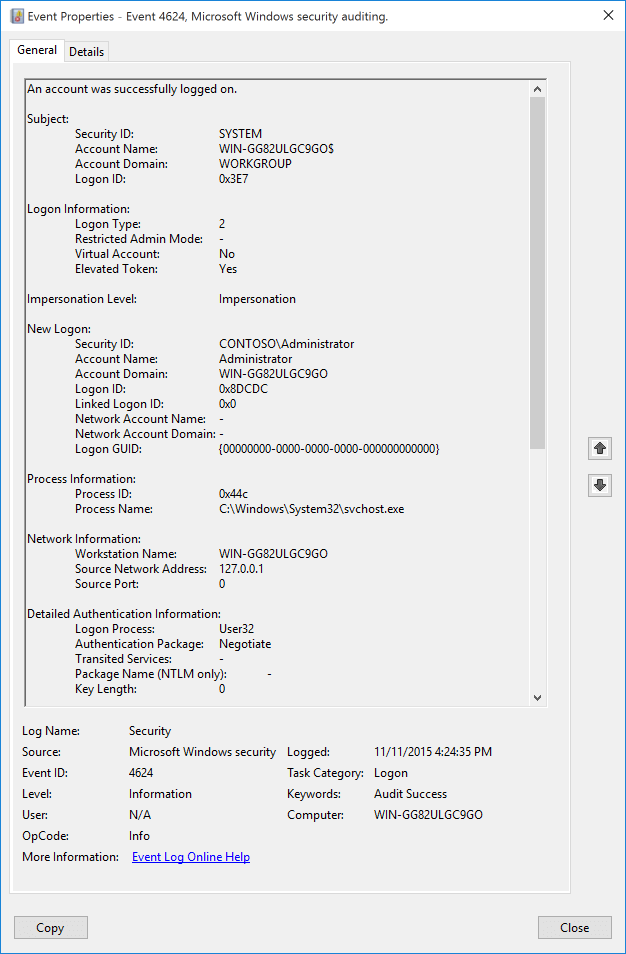
4624 S Un Compte A Ete Connecte Avec Succes Windows 10 Windows Security Microsoft Docs

4648 S A Logon Was Attempted Using Explicit Credentials Windows 10 Windows Security Microsoft Docs

Successful 4624 Anonymous Logons To Windows Server From External Ips

Microsoft Windows Security Auditing 4624 Anonymous Logon Windows Forkidslasopa

How Do I Interpret Id 4624 Type 3 Events On A Domain Controller Server Fault

Event Viewer Event Id 4624 See Who And When Logged Into My Computer Youtube
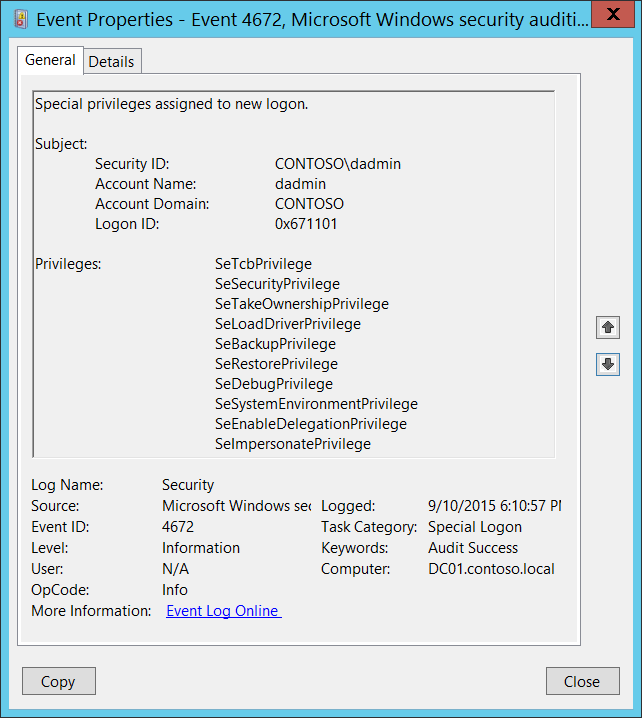
4672 S Special Privileges Assigned To New Logon Windows 10 Windows Security Microsoft Docs

4634 S An Account Was Logged Off Windows 10 Windows Security Microsoft Docs
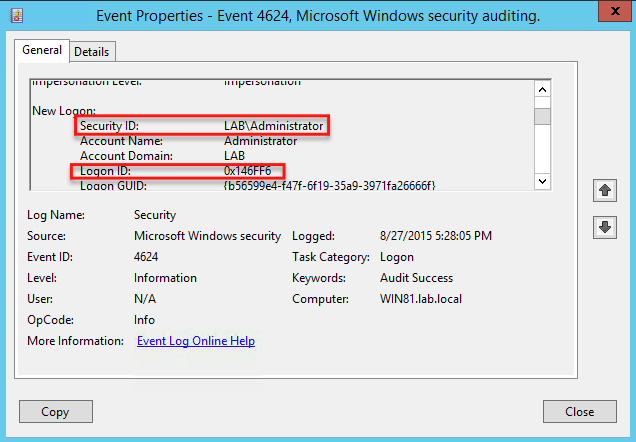
How To Get User Logon Session Times From The Event Log

4618 S A Monitored Security Event Pattern Has Occurred Windows 10 Windows Security Microsoft Docs

How To Get User Logon Session Times From The Event Log
Windows Event Id 4624 Inicio De Sesion Exitoso Guia Para Principiantes Lectura De 3 Minutos Mexico

Posting Komentar untuk "Event Id 4624"